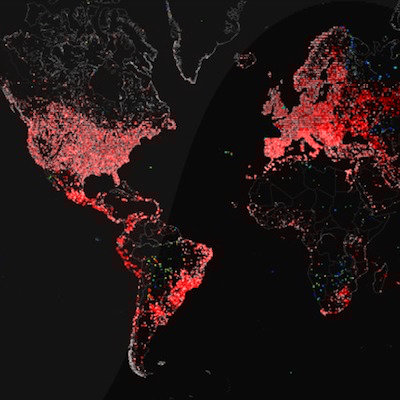
In 2012 the Carna botnet was built and unleashed on the world. But it didn’t have any intentions on doing anything malicious. It was built just to help us all understand the Internet better. This botnet used the oldest security vulnerability in the book. And the data that came out of it was amazing.
The Carna botnet was used to scan the internet to create a map of where all the public facing computer are in the world. The map it created is remarkable.
Click to view the animated map
Guest
Thanks to Parth Shukla from AUSCert for sharing his story. Parth’s research papers and Black Hat talk is below.
- Analysing the IPv4 Internet
- Compromised Devices of the Carna Botnet
- Parth’s talk at Deep Sec with much more in depth analysis
- Slides from Black Hat talk
References
- http://census2012.sourceforge.net/paper.html
- http://seclists.org/fulldisclosure/2013/Mar/166
- https://www.darkreading.com/vulnerabilities—threats/what-the-carna-botnet-also-found/d/d-id/1140892
- https://www.reddit.com/r/educationalgifs/comments/77ep8k/map_of_the_internets_pulse_based_on_time_of_day/
- https://www.caida.org/research/security/carna/
- http://www.sigcomm.org/sites/default/files/ccr/papers/2014/July/0000000-0000013.pdf
- https://www.cyber.nj.gov/threat-profiles/botnet-variants/aidra-botnet
- https://www.rapid7.com/db/vulnerabilities/telnet-default-account-admin-password-password
Music
Music in this episode: “The Loss of Blood” and “Blood Loss” by Ian Alex Mac. “Monkeys Spinning Monkeys” by Kevin MacLeod Licensed under Creative Commons: By Attribution 3.0 License. “The Confrontation”, “Quail and Robot Convo”, “Glitter”, “Bell Club”, “Gears Spinning”, “Skeptic”, “Undersea Garden”, “Puzzler”, “Chrome Muffler” and “Encounter” by Podington Bear.
Additional sound effects EM_magnetic_valve02.wav in this episode courtesy of holger.schwetter under Creative Commons attribution license.
Transcript
[FULL TRANSCRIPT]
JACK: [MUSIC] There’s a big list of all known security vulnerabilities for computers. You want to know what the oldest known computer vulnerability is? The oldest I could find is weak default passwords. This has been a known vulnerability since 1969. Specifically, computers sometimes have the username admin with the password also admin. Then the computer doesn’t ask you to change it when you buy it, so it can stay that way for a long time, years. Many computers after that also use admin/admin as the default username and password. Over the years many hackers have been able to get into many systems that they didn’t own using this basic username and password. Now it’s been forty years since we became aware of this security weakness. Surely by now this weakness has been resolved, right? There aren’t any computers in the world that have this username and password anymore, right? Right? I sure hope so.